
Innovation in Field Services Management
By: Elías Cedillo Hernández
CEO and Founder of GrupoBeIT, BuroMC, and Elite Infrastructure Services
GrupoBeIT developed its innovative model for field service management, called Field Services 2.0. This model goes beyond traditional field services by moving away from reactive actions toward providing more proactive solutions. It is supported by four fundamental pillars: People, Awareness, Technology, and Zero Trust Network Access, all framed within a vision of cybersecurity compliance and information protection.
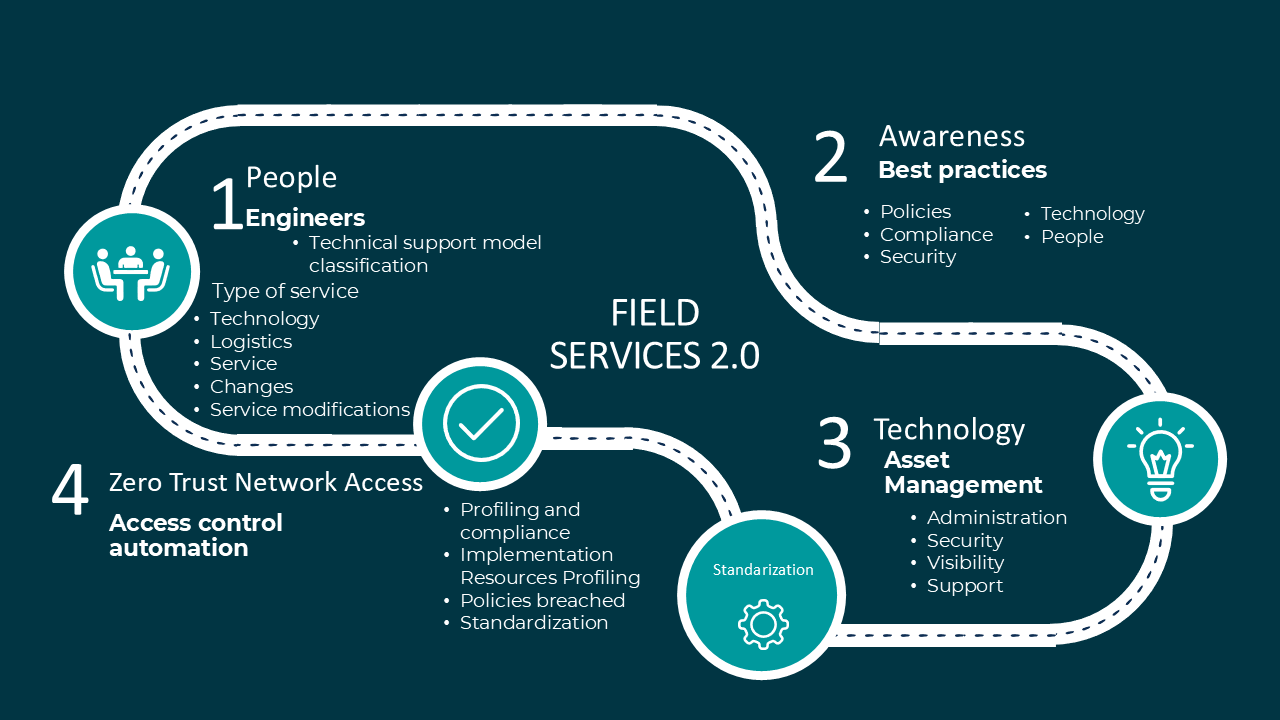
Within our Field Services 2.0 journey, we begin with the first pillar: People. This focuses on the human resource (engineers) and the classification within the technical support model. This process includes evaluating the type of service, the technology used, the logistics involved, and any changes in services. According to McKinsey & Company, proper classification and task assignment ensures that engineers are prepared to face any technical challenge efficiently and accurately, whether on-site or remotely.
The second pillar is Awareness, where the importance of good practices is highlighted. This includes clear policies, regulatory compliance, and security measures. Awareness and adherence to these practices are essential to maintain service integrity and quality, as well as to protect both employees and customers. Compliance with regulations, policies, and security measures requires a comprehensive review of data governance and offers an opportunity to reimagine the value. That can be provided. A thorough review of the data and how it is used allows organizations to define their current risk and proactively ensure they have the appropriate security processes and architecture in place. To illustrate this, consider the following example: a U.S.-based health insurer, valued at $60 billion, suffered a breach of 2.8 million protected health information (PHI) records when a laptop was stolen from a vendor. The total impact of the incident was $1.7 billion, and nearly 75% of that amount was due to lost revenue from contracts and loss of company and/or customer information. Now that we understand what our Awareness pillar may involve, how would a similar data breach affect your organization, and what measures are you taking to prevent it? Our third pillar, Technology, focuses on asset management. This pillar includes governance, security, visibility, and support of technological assets. Effective management of these resources ensures that field services are carried out safely and efficiently, providing a solid foundation for continuous operation and ongoing improvement. In 2024, KPMG in their research "Asset Management in Latin America" defined asset management as the pursuit of maximizing the value of assets throughout their lifecycle, aligning investment, operation, and maintenance decisions with the organization’s objectives. Among their findings, 51% of respondents believed that asset management helps reduce operational costs. Finally. Zero Trust Network Access, the fourth pillar, centers on automating access control (zero trust), ensuring that only authorized individuals can access the necessary resources and applications. Implementing this security model is crucial to protecting the organization’s infrastructure and sensitive data. Returning to the earlier example and creating a hypothetical scenario with these questions: What level of access did the vendor have? What level of access did the laptop user have? Did the device have the appropriate security for each resource? This is the perfect scenario created for any cyberattacker or intruder to carry out a digital breach of the organization, group, and/or company. Imagine for a few minutes that you are an executive at the company in the example. Fortinet, in one of its reports, revealed that 51% of organizations said their senior executives faced fines (34%), jail time (16%), and loss of position or employment (33%) after a cyberattack. Adding to this, 62% of leaders expect their employees to be victims of cyberattacks in 2025 due to the implementation of AI improving attackers' methods. In this case, the question would be: Do you believe a traditional model is still effective?
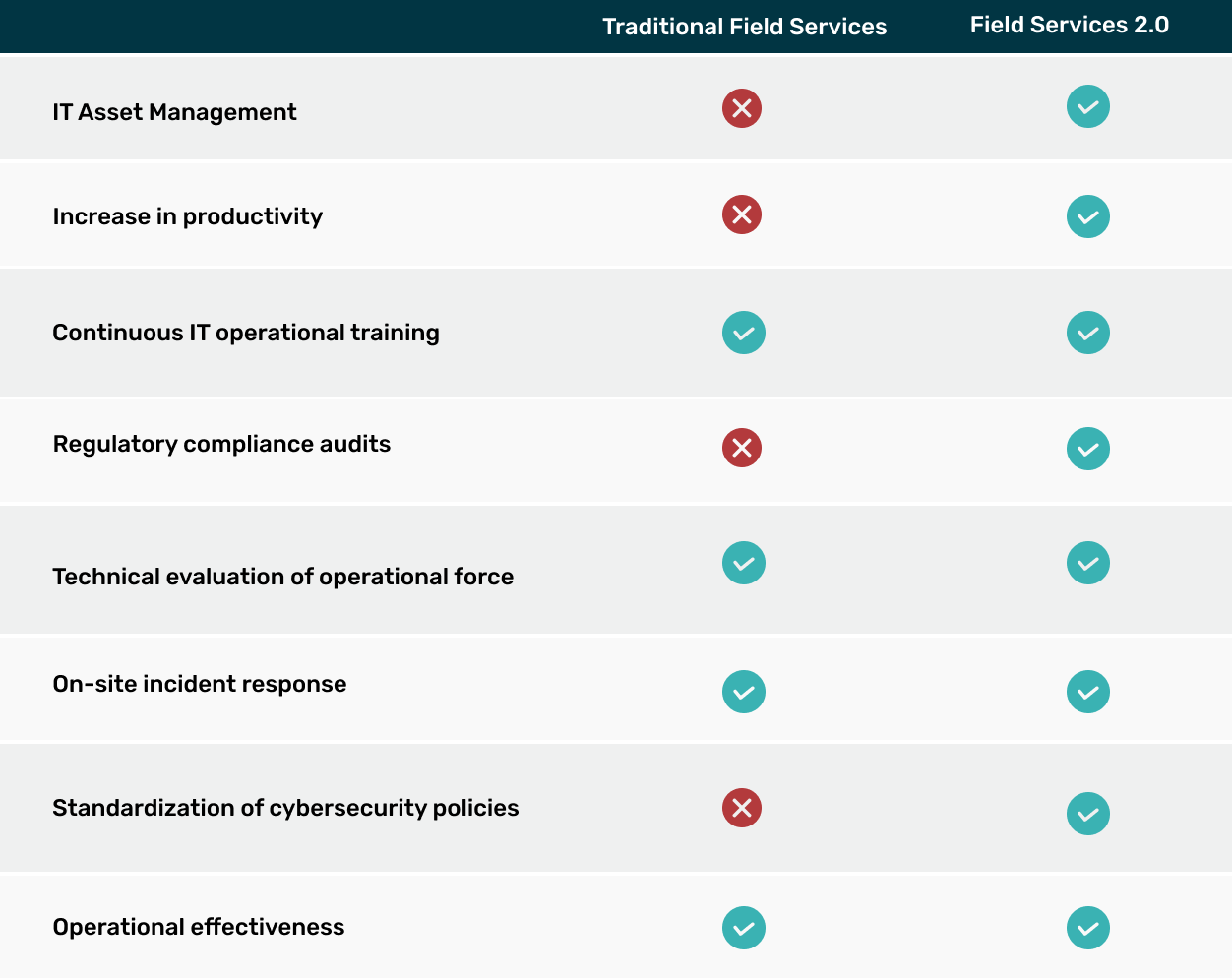
GrupoBeIT’s Field Services 2.0 represents a significant advancement in field service management by combining advanced technology, robust security practices, and efficient management of both human and technological resources. This comprehensive model not only improves service quality and customer satisfaction but also protects the organization from potential risks, optimizes operational efficiency, and strengthens the trust of clients and partners.












Post comments (0)